Gone Phishing
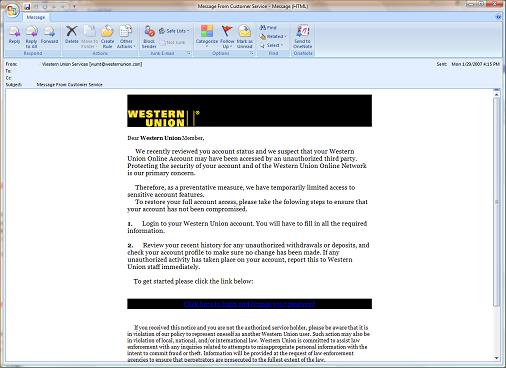
I got phished recently (I did not actually fall for the scam, I just got the e-mail). I am a very careful person when it comes to e-mail (bordering on paranoid), so I get very little SPAM and this is the first Phishing attack I have ever received.
Note: I got this phishing e-mail about a month ago and I waited to create this post until the phishing site was shut down - I did not want anyone to visit the site and get attacked. I wish (hind sight) that I had taken a screen shot of the site while it was up. 🙁
Quick Background on Phishing (Feel free to skip this section if you know all about it)
Phishing by e-mail relies upon the SPAM techniques to get you an e-mail. They spoof SMTP Headers, they change the “from” address so it looks like it is legitimately from a company that you trust (the one that I got was from Western Union) and they try to get you to open the e-mail with a catchy subject.
The intent with phishing is (generally) to get you to click on a link in the e-mail that will take you to a phony web site. They can do this with a number of techniques. This one uses a FUD style attack that makes you concerned that someone has compromised your account. Others will tell you “sign in to see if you win a prize”. Compare these 2 links:
https://wumt.westernunion.com/asp/regLogin.asp – the real Western Union login
http://wumt.westernunion.com.ref67.com/asp/regLogin.htm – the phishing site
If you just glance at the address it looks legit! If you click on the link you go to a site that looks exactly like the Western Union site and it asks you to login. If you do login, the phisher has your userid and password to the Western Union Site.
** But I am not a Western Union customer** My first clue to the fact that this was a phishing attack was that I am not a Western Union customer. But Western Union has a lot of customers and the phishing attack relies upon this. Let’s assume that they send 1,000,000 of these e-mails and that 1/10 of them get through the spam filters and to a real e-mail address (that is a conservative estimate). We are down to 100,000 potential victims. Let’s assume that 1% of the population has a Western Union Account and that 10% of those will fall completely for the attack. That is 100 accounts that will be compromised. If the phisher can get $100 from each of those victims that is $10,000 collected.
How do we stop phishing?
User Education – One of the key reasons that I am writing this entry is to continue the dialog to educate people about phishing. Most of the people who would find and read this blog are probably very technical, and they don’t need the information, but it might spur them to have the conversation with a family or friend who needs some education. User education only goes so far (but it does help).
Services that detect Phishing – Kudos to both Internet Explorer and Firefox for building in technology to detect and warn the user of the potential phishing attacks. Also Netcraft is an excellent source of research and detection of phishing sites.
Better password technology – Let’s suppose that web sites that are likely to be spoofed in phishing scams did not use plain text passwords. Let’s assume that they used encrypted tokens that were only valid for the site that they were sent to. So that if a phisher got a token for his spoofed site it was worthless on the real site. This is the true long term solution for phishing – industry standards like SAML and implementations that use them like Windows Cardspace.
I will be blogging more about SAML and Cardspace in the future, because I think they are important technologies that address the security challenges we are facing on the Internet.